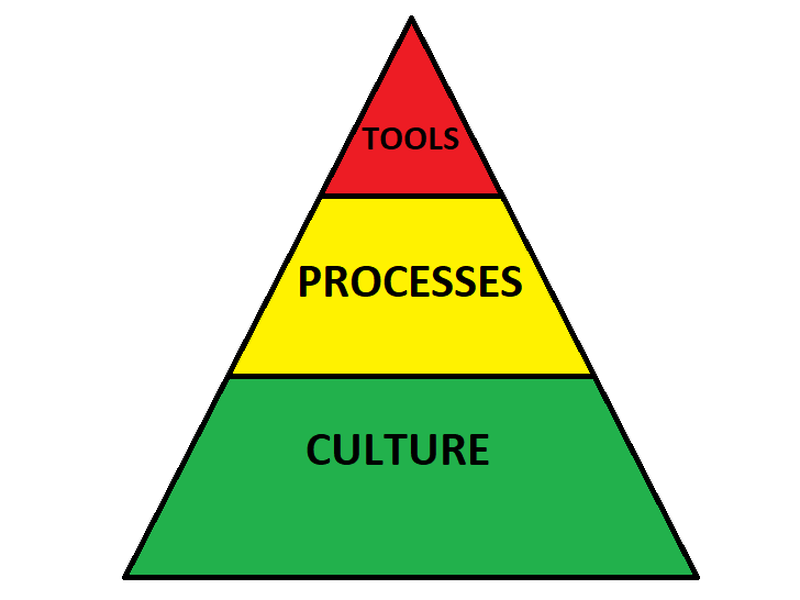
Security is about culture and process more than tools
Posted
There’s no question that data security becomes increasingly important on a daily basis, and with more information being pushed to the cloud, the topic is magnified. Unfortunately, many firms that sell security tools put their profits first, so instead of taking a risk-based approach, start spreading fear, uncertainty, and doubt, or FUD as it’s known in the industry. Don’t jump into buying a product unless you already have a good security foundation in your organization.
Let me be clear: Security begins with culture.
You can have the best processes and tools in the world, but if you don’t have an open culture to discuss concerns and admit mistakes, security will suffer. It’s important to empower every employee to speak out about issues they’re aware of so that those issues can be properly analyzed and prioritized. In addition, we are all human: Expect that people will make mistakes, but move quickly to contain and remediate those mistakes. Your culture should emphasize teamwork, collaboration, and openness, and always eschew blame.
When building the culture, don’t make it boring. You should have awareness trainings, for example, but don’t rely on mundane PowerPoint presentations. Make the awareness interactive whenever you can. This can include highlighting incidents that your organization has experienced and giving examples on ways to prevent them in the future. Bonus points for engaging the organization to obtain these ideas. Security does not rest solely with the security team.
Which brings up the next point on culture: Everyone is responsible for security, it’s not limited to the security team. When everyone feels like they’re part of the solution, you’ll in essence have human sensors thorughout the entire organization that will not only try to act with a security-focused mindset, but will also report issues they see directly to the security team, many times before you even see them within your toolset.
After culture: Build processes, don’t buy products (yet).
That’s not to say that quality security products can’t be used to help gain insights into potential threats or to help prevent malicious actors from accessing your data. There are many tools that improve the overall security posture of an organization, from scanners that look at infrastructure and applications for vulnerabilities, to firewalls that block bad traffic, to intrusion detection systems that identify and notify engineers of suspicious network traffic. The thing to remember is that just owning and using those tools doesn’t improve security very much. If I scan an application and identify a dozen vulnerabilities, but do not have a process in place to remediate those risks, the tool is useless. If I receive alerts of suspicious traffic, but do not have a process in place to investigate, the tool is useless. If I have a firewall that blocks all known bad traffic, but do not have a good program to protect data from insiders, the tool is useless.
Have you categorized your data, completed a risk assessment, and built a threat model for your organiation? If you don’t know what data you are protecting and what regulations are around that data, how will a tool protect you? If you haven’t identified risks to that data and don’t have a threat model defining how the data can be compromised, how do you know that a firewall is your best solution? These are some of the pieces of the puzzle that you have to put into place before you start thinking about tooling.
When doing your risk assessment and threat modeling, it’s important to look at third party suppliers as well. It’s becoming more common for malicious actors to target smaller third party vendors that may not have the same security maturity as your organiation as a way to gain a foothold into your environment. Do they have high quality security credentials, such as FedRAMP? If they do, have you asked them what your responsibility is? At the very least, you need to make sure the people who have access to these third party tools still need the access. When an employee leaves your organization, are you removing them from the SaaS tools?
After culture and processes: Now implement good tooling.
Now that you have your security culture in place (which will be an ongoing activity), and have defined processes in place to keep your systems safe, it’s time to identify what tooling you need, a topic that could span multiple articles in and of itself. Where you decide to invest will ultimately depend on the answers to the culture and process questions we looked at.
In short, just remember that security tools are but a small piece of the puzzle. You must have a strong security culture at your organization’s foundation, and a robust set of processes built upon that culture. Only then can you supplement with tools that will help make your organization truly secure.